Call records, chat correspondence, CRM forms store not only the name and phone of the client, but also more vulnerable information: address, passport details, financial accounts, etc. Data protection is an important element of call center operations, but if the information falls into the network or into the hands of malicious individuals, you can forget about customer trust. In this article, we will explain what is cybersecurity, what threats exist, and how using Oki-Toki can secure your data.
Cybersecurity and its importance for call centers
Cybersecurity definition refers to the actions taken to protect personal data regarding the company and its clients.. It is the duty of call centers to secure information about calls, forms, user access to the system, and API keys for integrations.
Ensuring data security has become more difficult because:
- employees work from various devices and locations;
- they use multiple communication channels: calls, chats, social networks, email;
All of this increases the opportunities for cyberattacks and fraud. To avoid data or access loss, call centers face the important task of organizing a comprehensive approach to security policy.
Cybersecurity threats in real work
Security threats in the call center can be conditionally divided into two types:
External threats – attempts of hacking and deception “from outside” to gain access to the system or confidential information. This could be:
- Phishing or malicious emails – an employee receives an email with a link or attachment through mail or in the work chat. After clicking on the link, a malicious program opens access to personal information.
- Social engineering – fraudsters do not hack the system, but deceive a person. They call or write, can pretend to be a colleague from another department or the director. Their goal is to gain trust and make the employee reveal passwords or pass on client data.
External attacks are the result of human error. Training and additional education of employees will help learn to notice threats in time and not fall for the trick.
Internal threats – consequences of incorrect settings and actions within the company. These can include:
- Weak passwords – easy to guess, meaning the possibility of entering the system;
- Access after dismissal – if the account of a former employee is not blocked, he may use internal information for personal purposes;
- Access rights – if a user has more rights than needed for their duties, the risk of confidential data leakage increases.
Cybersecurity threats do not require special technical knowledge, but without attention to them, no data leak protection will work effectively.
Where security begins?
Registering a new user in Oki-Toki
You can add an employee if you have the “User management” right. Sending an invitation requires only an email – issue the new employee a corporate email (if provided) or let them provide their own.
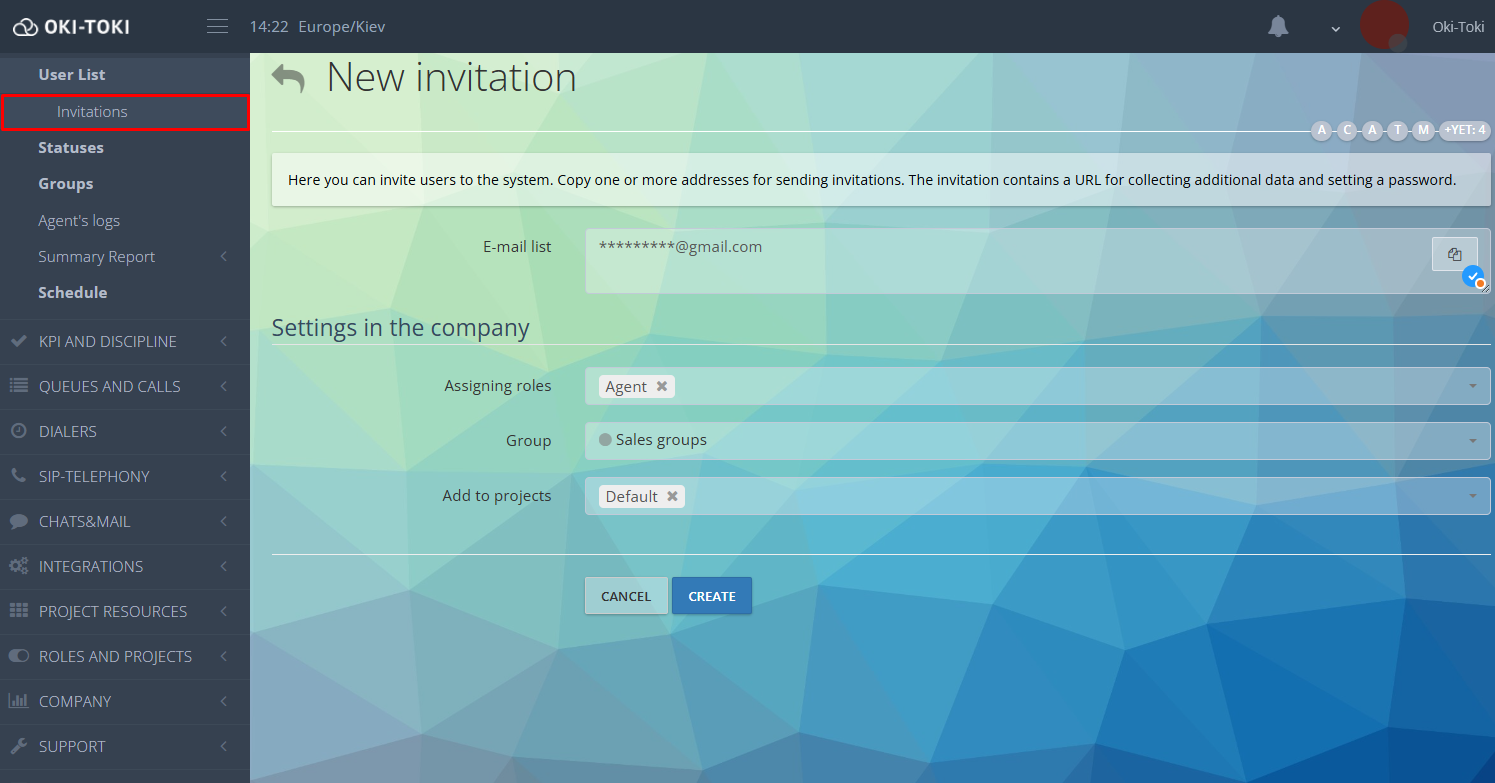
The user has 7 days to confirm registration and log into the system.
What is required from the new employee upon registration:
- A truly strong password. The variety of signs (numbers, uppercase and lowercase letters, special symbols) increases the number of possible combinations when auto-selecting a password – millions of possibilities.
- Prevent password leakage or transfer to third parties. The access code should remain confidential. Do not pass it to colleagues, store in browsers, or use the auto-login feature on devices accessible by others. Do not write passwords on paper or in unencrypted files on the computer.
- Trust modern password storage services – “Google password manager”, “Bitwarden”, “Lastpass” and so on.
A strong password – the first and very important stage of security in contact centers.
Access management: roles and projects
“Roles” define user permissions in the system. For example, an agent sees only their own calls and widget data, while a supervisor sees statistics and reports. You can use default roles “Admin”, “Agent”, “Supervisor” or create your own. A role is determined at the moment of user invitation so they have access only to the necessary sections.
With “Projects” you can divide work according to different business processes or company tasks, isolating them from each other. Users will only see data pertaining to their directions. This helps control employee access and maintain confidentiality. The right “See everything, regardless of projects” provides access to all data. By default, this permission is included in the “Admin” role.
What to do with dismissed employee’s access?
If the employee will no longer work at your company – it’s important to immediately disconnect them from the service. By using the “Access to system” checkbox in the user’s profile, you can block the ability to log in while preserving the data about their work.
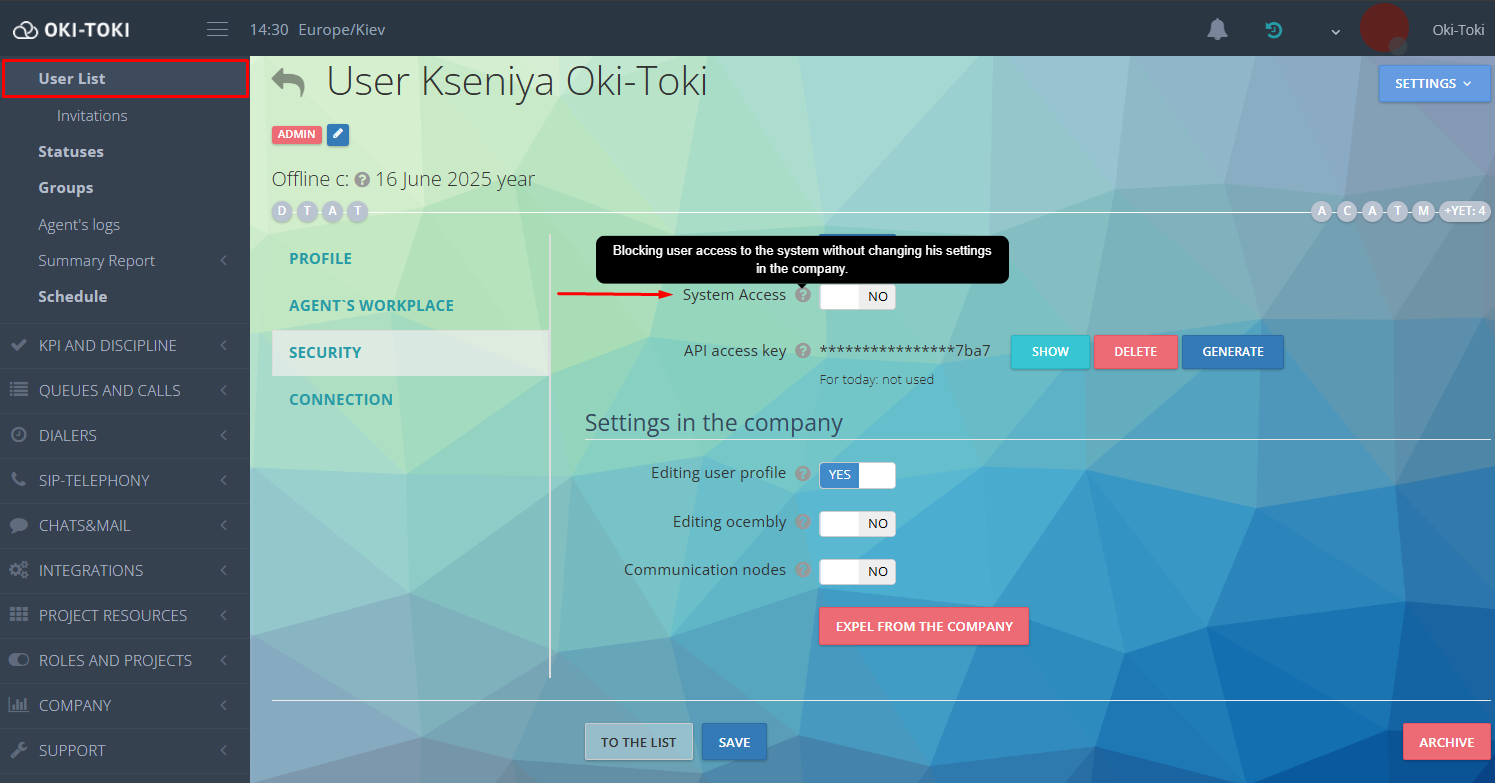
Once the reports are collected — transfer the user to the archive. After the data retention period expires, archived users will be automatically deleted. To manually remove an employee, you can exclude them from the company, but it is important to remember that you cannot collect reports after this action.
Useful security options in Oki-Toki.
For contact center security, protecting the personal information of clients is not just a requirement but a duty. In Oki-Toki, there are many options that create additional levels of protection and help control access to data. Let’s look at each solution in detail.
Integration with social networks
For logging into the system, you can use a Google or Facebook account. Linking the account is available in the profile settings.
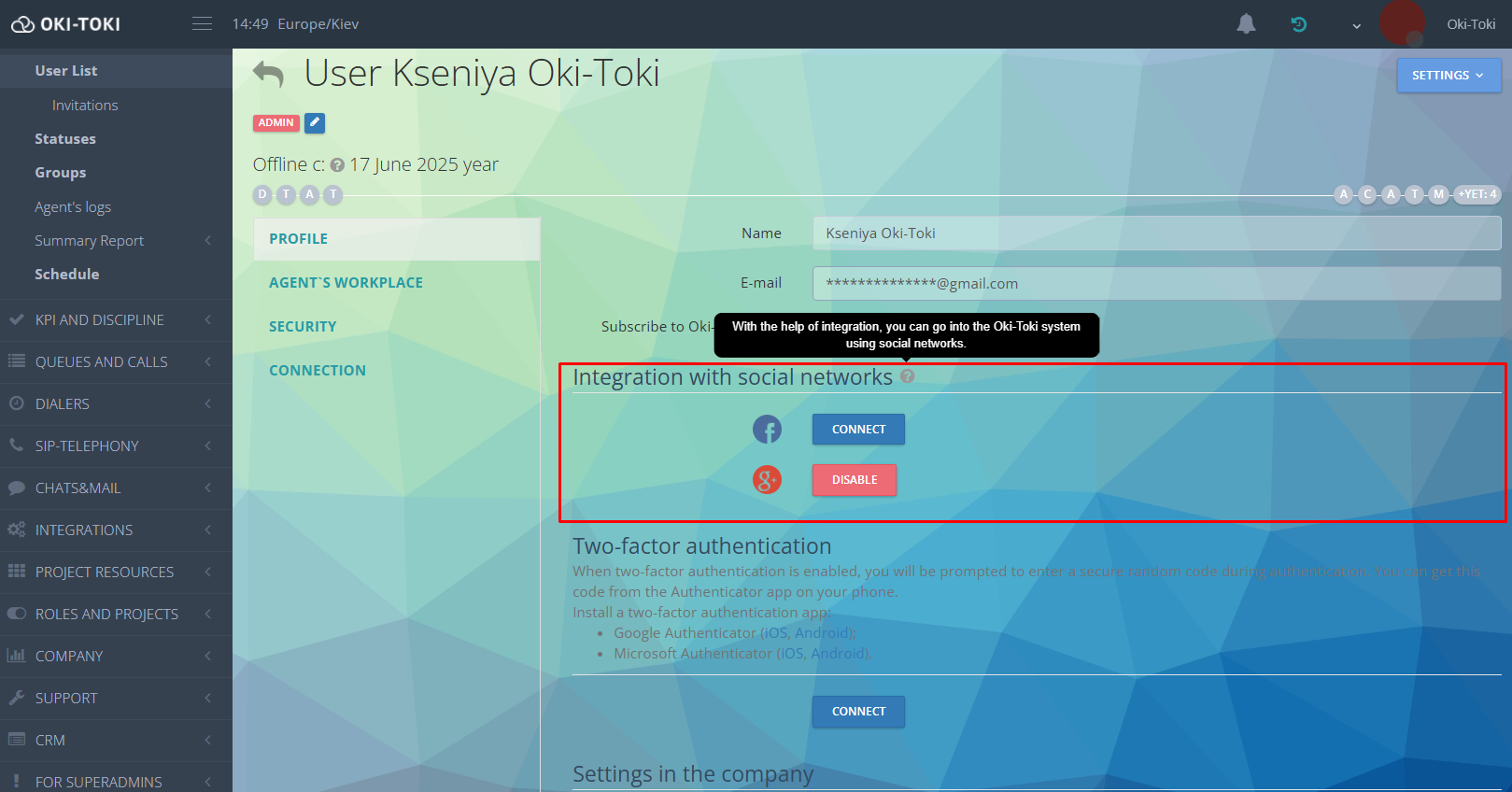
After connecting, an email will be sent to confirm. Now you can log into the system using the social network or a regular password.Why is this needed? First, it’s convenient – fewer data for login, fewer reasons to forget a password. Second, it’s safe: Google and Facebook use their own security systems, and you essentially transfer this protection to your access to Oki-Toki.
Two-factor authentication (2FA)
“Two-factor authentication” is an additional identity confirmation through an authorized app on your phone. Even if the password is stolen, entry will not be possible without the code.To connect 2FA, go to user settings and download “Google Authenticator” or “Microsoft Authenticator” to your phone. Choose the app and version for Android or IOS. After installing the app, press the “Connect” button to activate authentication.
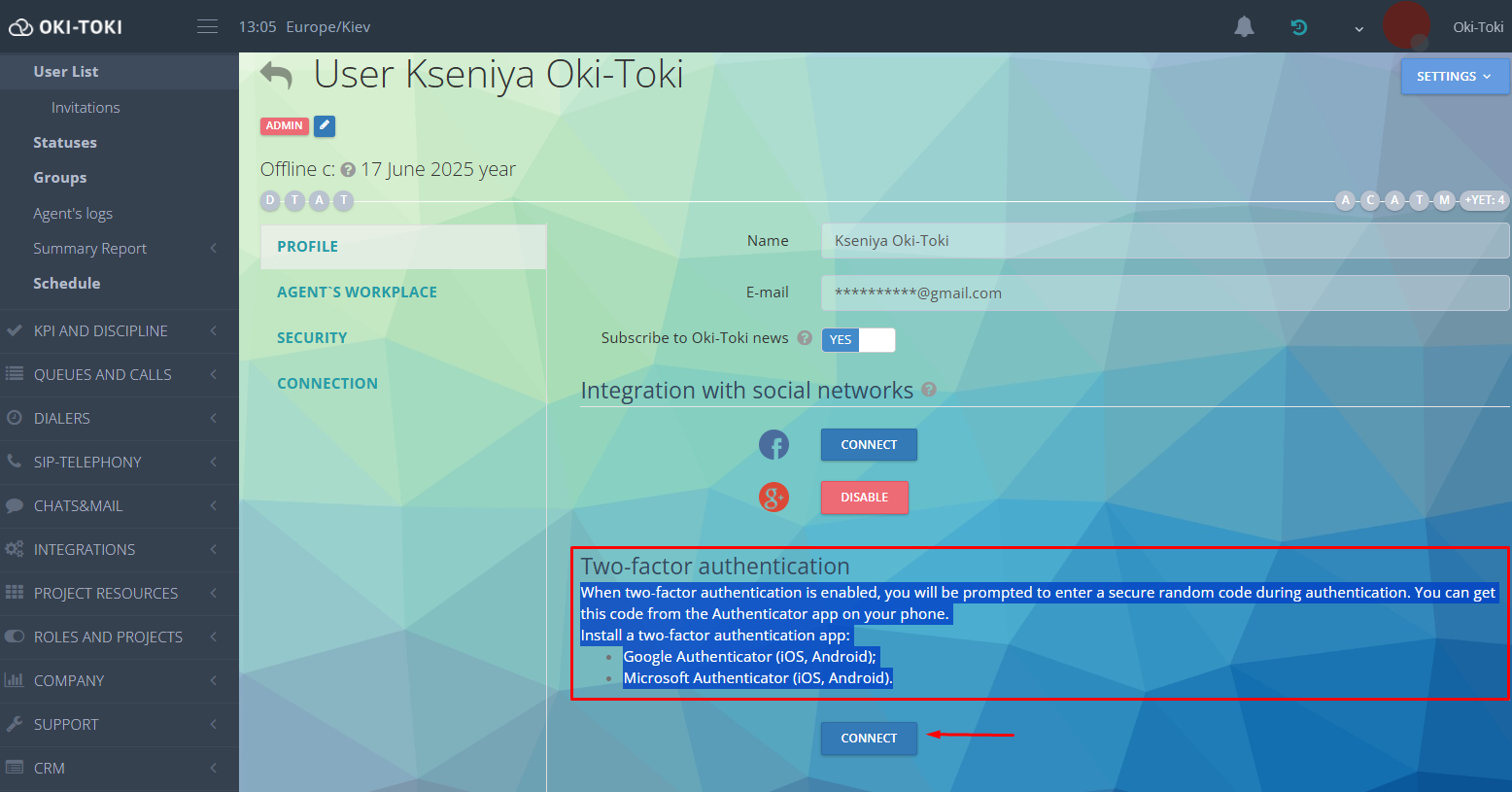
Now, when trying to log into the account, you will need to enter the code from the app. If the user has the right “Edit profile,” disabling two-factor authentication is possible at any time. Disabling the feature for other employees is permitted with the “User management” right.
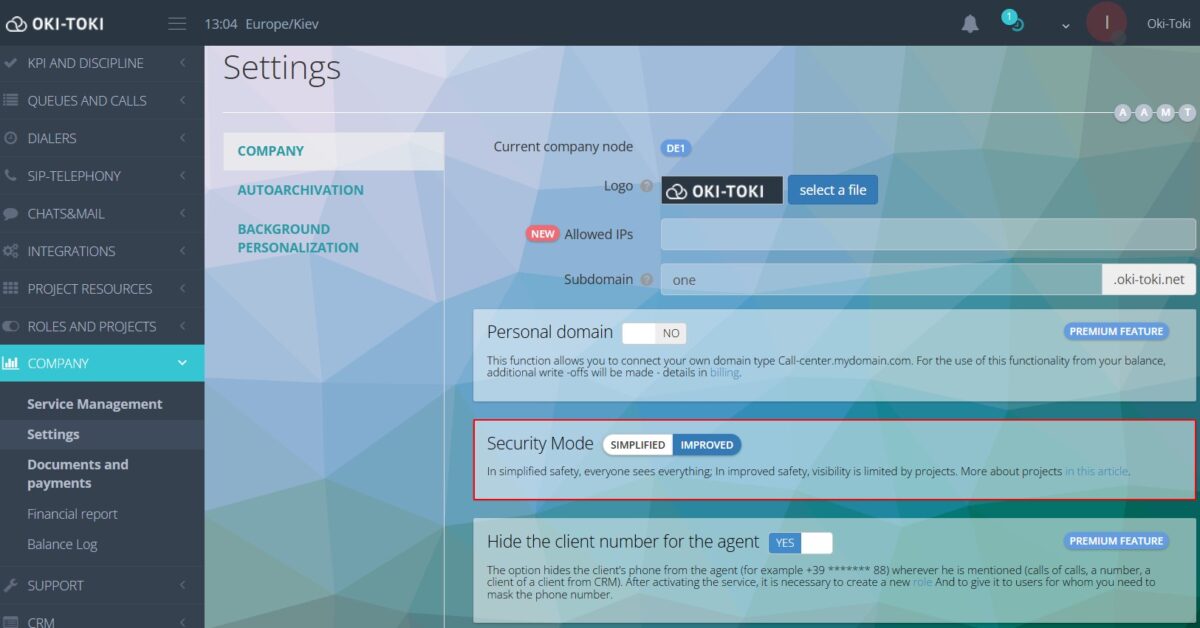
Login from allowed IP Aaddresses
Limiting by IP means that connection to the system is allowed only from specific addresses. For example, from the office internet. This can exclude attempts to access from other devices or networks. You can enter a list of trusted IPs in company settings. Specify one or several addresses from which users can log into Oki-Toki. This is an additional level of security that is worth using if the company has fixed workplaces and a constant IP address.
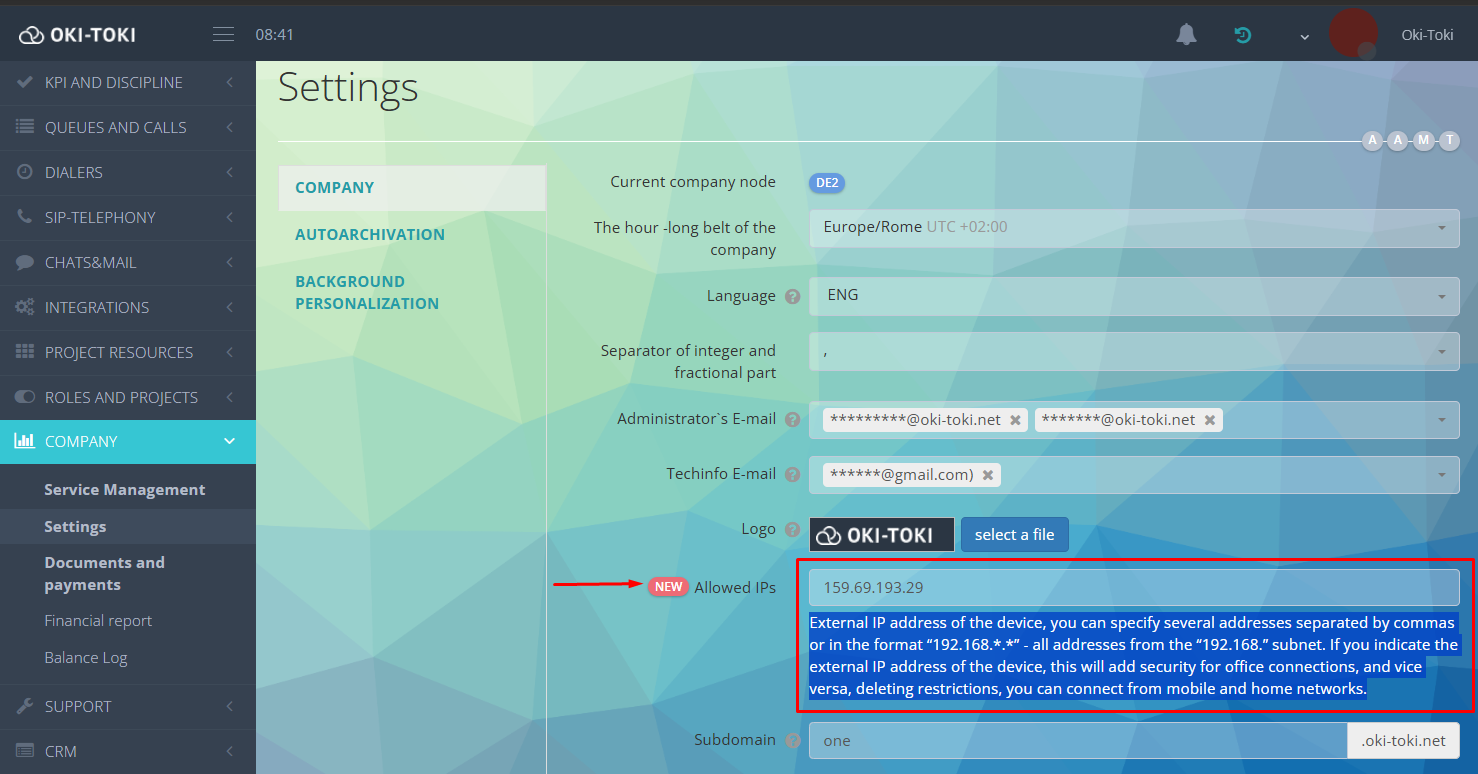
If your company has IP restriction enabled, but some employees need access from any address, this can be configured through roles. Activate the option “Ignore allowed IPs”, and such users will be able to log into the system from any IP address.
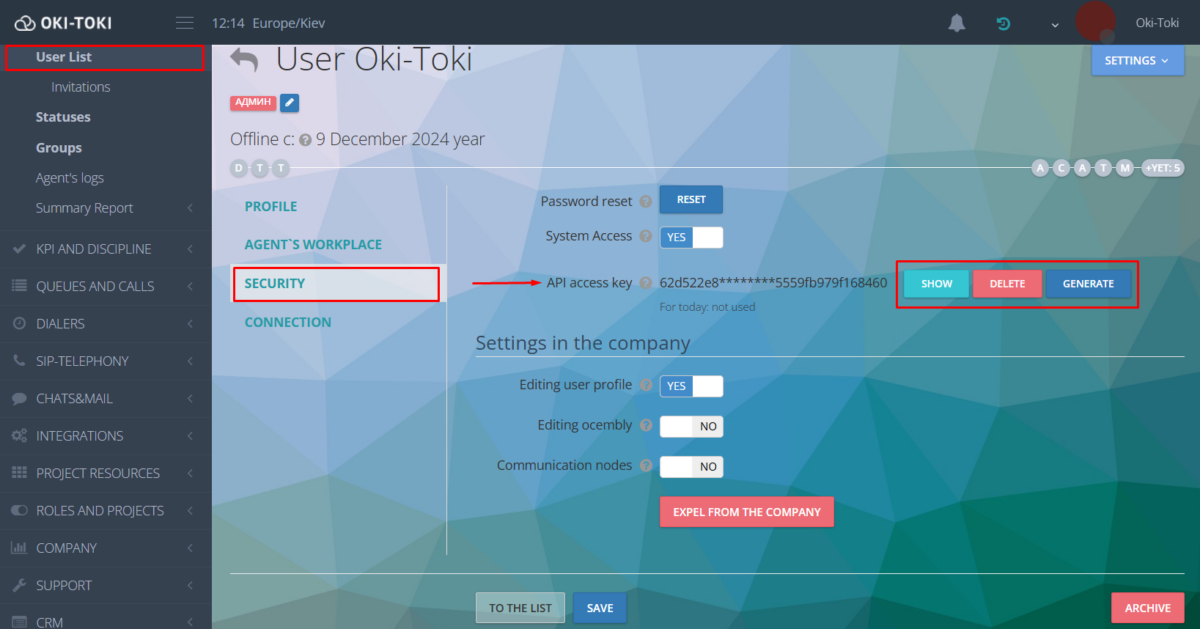
API keys and their security
API (Application Programming Interface) is a tool for integration with other servers and services. It allows exchanging data or performing simple operations for business processes – for example, integration with CRM. Access to data exchange is protected by a key called “API Token”. Such a key can be generated for an employee in profile settings.
Security of API keys in Oki-Toki is implemented as follows:
- Limited access by role and project – the token can only be used with the right “Manage external resources, integrations, and events (Webhook)” and only within the project the member is part of;
- Token limit – only one API-key can be generated for a user;
- Logging of API calls in reports, each API request is recorded in the “Action Log”;
- Daily statistics of token usage collected in the “API Usage” widget in the “Service Management” section.
Hiding the client’s number from the agent
This option hides the phone number of the client from the agent, showing it as partially masked (for example, +39*******88). The number is hidden in call history, dialer, and CRM form.To use this option, create a new role for agents, where the right “See masked fields” will be inactive. In this case, users will only see part of the number. Thus, the likelihood of lead and client database leakage through the agent’s place is minimized.
Important! Data in reports remains open, so agents should not have access to call center reporting in the personal cabinet.
Monitoring users and actions in Oki-Toki
Despite the various options for protecting the workplace, leaks are still possible through the “Personal Cabinet”. “Supervisor”, “Administrator”, or “Agent” with excessive rights can listen, download recordings, and export reports. It’s impossible to protect from report and record exports in such cases, but performed actions are thoroughly logged.
In Oki-Toki, you can monitor different user actions with reports:
- Change log – an additional panel with data about who and when made changes in any section of thesystem. Access to view logs is provided by the right “View change log”, available by default for the “Admin” role.
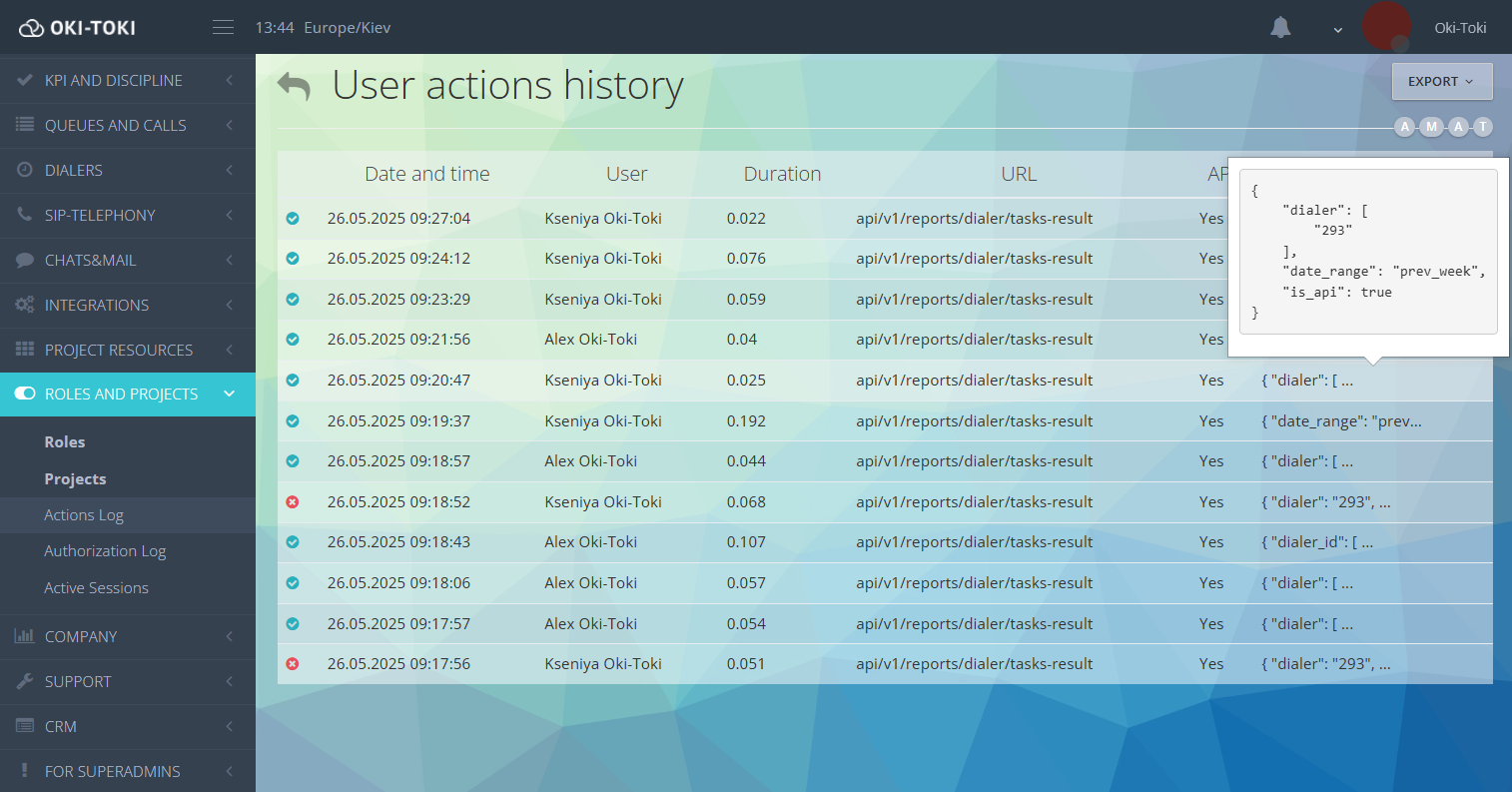
- Action log – this contains information about the activity of employees in Oki-Toki. It records both standard actions in the system and API requests. Searching is available by period, user, or type of request. The generated report will display information about the user, the exact time of command execution, the URL of the page where the action was performed, and the API call parameters.
- Active sessions – a report consisting of two sections:
- “Administrative interface” – data about the user, their role, IP address, the last URL they visited, and the time;
- “Agent workplace” – information about agents, statuses at the workspace, and time spent in them, the name of the queue/dialer, and call id if there are active dialogs.
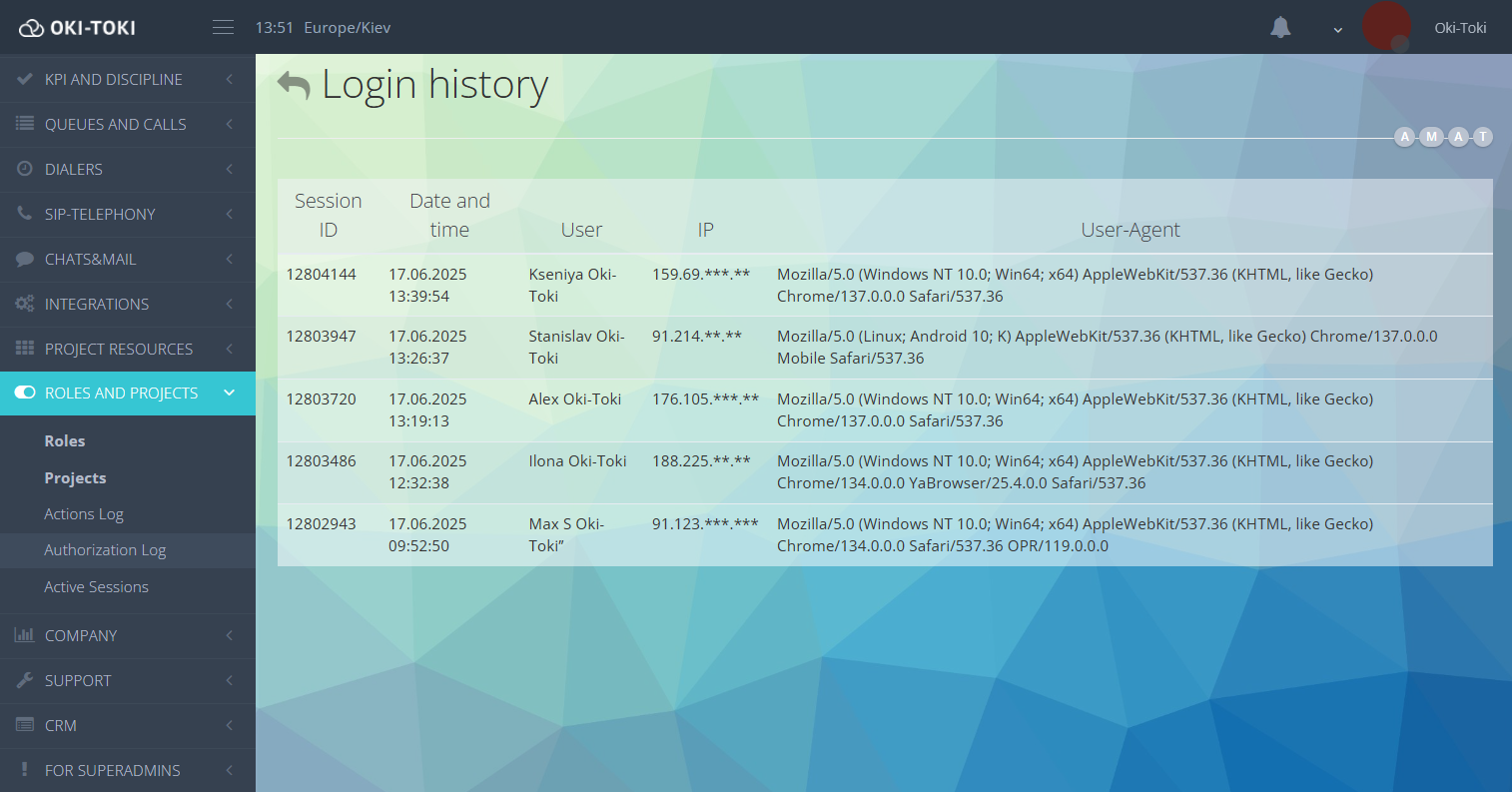
- Login log – it collects information about user logins into the system: date, time, IP address, browser name, and its version.
- Listening to audio recordings – information about who listened to or exported an audio file is collected in the action history with audio recordings in the Call log.
Cybersecurity and data protection are part of the security of a call center. It is important to remember that accesses and rights should correspond to the duties of the employee, and actions should be logged in the system. Implement additional security options, let it be a rule rather than an exception. This will help reduce risks, and most importantly, maintain customers’ trust in the company.